Google announced ICS Android 4.0 Ice Cream Sandwich a couple of months back, and so far it has managed to ship a single device with this new OS, the Galaxy Nexus. The second device to get an ICS 4.0 update was the old Google Nexus S, but OTA updates for the Nexus have been suspended due to technical issues. There is still no third device with ICS on board and we won’t see any for at least a few weeks.Companies are now announcing their own ICS upgrade schedules. LG says that their top devices get ICS in Q2 2012 (April 1 to June 30), while others will have to wait a few more months. Sony Ericsson should have ICS around Q2, if not earlier. Motorola and Samsung are reportedly scheduled to start updating their devices in Q1, but the process will inevitably drag on well into Q2. Worse, Samsung won’t roll out an ICS update for the Galaxy S, which sold in record numbers last year and it’s still a pretty nice phone with an affordable price tag.
In best case scenario, we might see some Android 2.3 to 4.0 update in Q1 but the best chance is to see some new phones launching with Ice Cream Sandwich at the Mobile World Conference, in Barcelona in last days of February.
Apple has IOS 5 in all of its phones capable of supporting the new OS for months now and at least the top two iPhones today, if not the top three, will get an update to the next version, guaranteed. Microsoft is also doing a pretty good job in the update department with Mango.
Mike Qaissaunee, a Professor of Engineering and Technology at Brookdale Community College in Lincroft, New Jersey, shares his experiences and perspectives on integrating new technologies in and approaches to teaching and learning. ~ Subscribe to this Blog
Saturday, December 31, 2011
Android Updates Taking Forever
Friday, December 30, 2011
Sir Jonathan Ive
Josh Ong reporting ... Apple design chief Jonathan Ive awarded knighthood
Jonathan Ive, Apple's senior vice president of industrial design, has been named a Knight Commander of the British Empire in the U.K.'s 2012 New Year Honours list, an honor he has described as "absolutely thrilling."
The BBC reported on Friday that Ive can now go by "Sir Jonathan." The knighthood, which is for "services to design and enterprise," is a step up from his previous title of Commander of the British Empire, which was awarded in 2005.
Ive responded that he was "both humbled and sincerely grateful" by the commendation.
- Posted using BlogPress from my iPad
Inventor of the Digital Camera
Not exactly portable, but amazing for 1975!

It’s been way too long since I’ve posted one of these. This is my portrait of Steven Sasson, inventor of the digital camera. He was the 32nd inventor in my project. I shot him in October at Kodak’s headquarters in Rochester, just a couple weeks before President Obama awarded him the National Medal of Technology.
Inventor Portrait: Steven Sasson from David Friedman on Vimeo.
- Posted using BlogPress from my iPad
Thursday, December 29, 2011
Something to Truly Disrupt Higher Education
James Marshall Crotty reporting … M.I.T. Game-Changer: Free Online Education For All
For Wall Street Occupiers or other decriers of the “social injustice” of college tuition, here’s a curveball bound to scramble your worldview: a totally free college education regardless of your academic performance or background. The Massachusetts Institute of Technology (M.I.T.) will announce on Monday that they intend to launch an online learning initiative called M.I.T.x,which will offer the online teaching of M.I.T. courses free of charge to anyone in the world.
The program will not allow students to earn an M.I.T. degree. Instead, those who are able to exhibit a mastery of the subjects taught on the platform will receive an official certificate of completion. The certificate will obviously not carry the weight of a traditional M.I.T. diploma, but it will provide an incentive to finish the online material. According to the New York Times, in order to prevent confusion, the certificate will be a credential bearing the distinct name of a new not-for-profit body that will be created within M.I.T.
…
Students using the program will be able to communicate with their peers through student-to-student discussions, allowing them an opportunity to ask questions or simply brainstorm with others, while also being able to access online laboratories and self-assessments. In the future, students and faculty will be able to control which classes will be available on the system based on their interests, creating a personalized education setting.
Wednesday, December 28, 2011
Tuesday, December 27, 2011
Apple Granted a Critical Multitouch Patent
Mikey Campbell reporting - Apple granted another key multitouch patent
Apple won a core multitouch patent regarding oscillating signals that was alluded to when Steve Jobs first announced the original iPhone in 2007, and adds to the company's already formidable legal arsenal.
The United States Patent and Trademark Office published on Tuesday that the Cupertino, Calif. company now owns a crucial patent that describes how touch events are recognized by a touchscreen device, and was one of the "200+ Patents for new inventions" Jobs lauded when the iPhone first debuted, reports Apple patent blog Patently Apple.
The newly granted patent focuses on the oscillator signal and circuit of a touchscreen-equipped device, an integral invention directly related to how users interact with their multitouch products.
...
The patent wording states that the invention could apply to computing devices such as desktops, laptops, tablets or handhelds, including digital music and video players and mobile telephones. Also mentioned are public computing systems like kiosks and ATMs.
- Posted using BlogPress from my iPad
Monday, December 26, 2011
New Years' Resoultion - Stronger Passwords
Since 2012 is the year of malware and cyber-espionage, here's a post from Dennis O'Reilly on How To Master The Art Of Passwords:
Considering the number of times PC users sign into a service or network each day, we may need to remember a half-dozen hard-to-guess passwords, not to mention the various sign-in IDs we use along with the passwords (full name or first initial-last name? Case sensitive? An e-mail address?). Many computer professionals need access to dozens of secure systems, which stretches the limits of anyone's memory.Your three options are to use a password-management program, to write your passwords down on paper (or record them in an encrypted text file), or to devise a method for memorizing hard-to-guess passphrases. While no single technique is right for everyone, here's why I suggest the memorization approach.
If you've still got some gifts to give, here's a way to give the gift of security – SplashID Key Safe – a flash drive with SplashID software built-in for Macs and PCs.Other alternatives are 1Password and LastPass.

2012 - a Big Year for Malware and Cyber-Espionage
The security industry expects the number of cyber-espionage attacks to increase in 2012 and the malware used for this purpose to become increasingly sophisticated....
"I absolutely expect this trend to continue through 2012 and beyond," said Rik Ferguson, director of security research and communication at security firm Trend Micro. "Espionage activities have, for hundreds of years, taken advantage of cutting-edge technologies to carry out covert operations; 2011 was not the beginning of Internet-facilitated espionage, nor will it be the end," he added.
Threats like Stuxnet, which is credited with setting back Iran's nuclear program by several years, or its successor, Duqu, have shocked the security industry with their level of sophistication. Experts believe that they are only the beginning and that more highly advanced malware will be launched in 2012.
Sunday, December 25, 2011
Last Minute Gifts
Happy holidays everyone. If you've still got some shopping to do or overlooked someone, there's still an opportunity to get them something today – as long as it's digital!
From Dave LeClair … Amazon Adds ‘Best Of’ Store To Recommend The Best Digital Items [News]:
If you are a last-minute Christmas shopper then this is the story for you. It’s now obviously too late to get anything shipped which is why Amazon has created their best of store, specifically to recommend the best items that can be purchased digitally. With a digital purchase there is no shipping, so you can still buy something on Christmas Day.
Saturday, December 24, 2011
802.11 Packets in Packets
New to 2011, Packet-in-Packet exploits allow for injection of raw radio frames into remote wireless networks. In these exploits, an attacker crafts a string that when transmitted over the air creates the symbols of a complete and valid radio packet. When radio interference damages the beginning of the outer packet, the receiver is tricked into seeing only the inner packet, allowing a frame to be remotely injected. The attacker requires no radio, and injection occurs without a software or hardware bug.
This lecture presents the first implementation of Packet-in-Packet injection for 802.11B, allowing malicious PHY-Layer frames to be remotely injected. The attack is standards-compliant and compatible with all vendors and drivers.
Unlike the simpler implementations for 802.15.4 and 2FSK, 802.11B presents a number of unique challenges to the PIP implementer. A single packet can use up to three symbol sets and three data-rates, switching rates once within the header and a second time for the beginning of the body. Additionally, a 7-bit scrambler randomizes the encoding of each packet, so the same string of text can be represented 128 different ways at the exact same rate and encoding.
This lecture presents the first implementation of Packet-in-Packet injection for 802.11B, allowing malicious PHY-Layer frames to be remotely injected. The attack is standards-compliant and compatible with all vendors and drivers.
- Posted using BlogPress from my iPad
Friday, December 23, 2011
More on Self-Healing Electronics
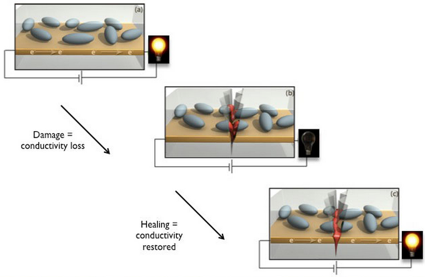
Self-healing electronics restores broken connection in microseconds | KurzweilAI:
University of Illinois engineers have developed a self-healing system that restores electrical conductivity to a cracked circuit in microseconds.“It simplifies the system,” said chemistry professor Jeffrey Moore, a co-author of the paper. “Rather than having to build in redundancies or to build in a sensory diagnostics system, this material is designed to take care of the problem itself.”
Self-Healing Circuits
Jamie Condliffe reporting – Self-Healing Circuits Use Liquid Metal To Turn Electronics Into Superheroes:
[Researchers have] developed a way to create printed circuits that can heal themselves using liquid metal. The best bit is that, unlike X-Men, this is real.So how the hell does it work? Essentially, the scientists have created tiny micro-capsules that contain liquid metal. When a printed circuit is made, a thin layer of these capsules can also be printed on top of the conventional strip of metal.
If a small crack forms in the printed circuit, usually that crack breaks the circuit. But with the micro-capsules in place, as the crack propagates some of the capsules are wrenched open, in turn releasing a small amount of liquid metal. That metal is enough to bridge the gap and keep the circuit working.
The End of the Digital Divide?
IBM thinks it's five years away.
Michael Cooney reporting … IBM Predicts Five Big Technologies of the Future:
Digital divide? In five years, the gap between information haves and have-nots will narrow considerably due to advances in mobile technology. There are 7 billion people inhabiting the world today. In five years there will be 5.6 billion mobile devices sold -- which means 80% of the current global population would each have a mobile device.
Thursday, December 22, 2011
Boy Genius Report's on RIM's Woes
According in Jonathan S. Geller things are even worse than they appear – BlackBerry 10 is a failure that won't be able to compete, company source says:
Our source has communicated to us in no uncertain terms that the PlayBook 2.0 OS developers have been testing is a crystal clear window into the current state of BlackBerry 10 on smartphones. No email, no BlackBerry Messenger — it’s almost identical. “Email and PIM [is better] on an 8700 than it is on BlackBerry 10,” our contact said while talking to us about RIM’s failure to make the company’s new OS work with the network infrastructure RIM is known for.We also have some more background on why RIM’s BlackBerry 10 smartphones are delayed, and it has nothing to do with a new LTE chipset that RIM is waiting on. In what is something of a serious allegation, our source told us that Mike Lazaridis was lying when he said the company’s new lineup was delayed for that reason. ”RIM is simply pushing this out as long as they can for one reason, they don’t have a working product yet,” we were told.
At the end of our conversation, our source communicated something shocking for a high-level RIM employee to say. He told us that RIM is betting its business on a platform and ecosystem that isn’t even as good as iPhone OS 1.0 or Android 2.0. “There’s no room for a fourth ecosystem,” he stated, “and DingleBerry also works on BlackBerry 10.”
Wednesday, December 21, 2011
The Future of Microsoft
Ben Brooks in Microsoft’s iOS Apps has an interesting thought about Microsoft's future. He's right that this won't happen with Ballmer as CEO. But there are even bigger issues.
Any revenue from iOS apps is just a rounding error on their (Microsoft's) balance sheets, so this is not disruptive to their core business (Windows and Office) in any way. What MS needs is a new revenue stream that has the potential to rival what they make from Office and Windows. I agree that – long-term – the Windows and Office businesses will continue to stagnate, but even stagnant Windows and Office will remain cash cows for a long time. How long? No one really knows, but apps are not the solution.
Like Apple's AppleTV, you can think of MS apps as a hobby.
If we go by a favorite saying of the tech web, that Office is far more important to Microsoft than Windows, would it not make sense then that 10 years from now Microsoft is just a really good “app” company?
That is, instead of making platforms (like Windows) they are just producing applications that run on the best platforms out there — regardless of who controls these platforms?
With Ballmer this won’t happen, but with fresh eyes this seems to be a pretty interesting strategy for a company that is struggling to get a foothold in the ever important mobile industry.
Of course this minimizes the sheer size of Windows itself, but then again I have to wonder just how important the traditional PC will be to the average consumer in a decade’s time.
Tuesday, December 20, 2011
Another Patent Threat to Google
From Mark Brown – BT Sues Google for Patent Infringements in Android, Maps, Google+ and More
The British phone company says, in its US-filed lawsuit, that Google has infringed on these patents in the Android operating system, apps on the Android Market, Google Maps, Docs, Music and Offers, various location-based services and most of its advertising empire.
An example patent is “Service provision system for communications networks,” which BT was awarded in the 1990s. It essentially boils down to an app figuring out whether a phone is connected to the web via Wi-Fi or 3G, and choosing to stream at a different bandwidth. Google infringes this in Google Music and the Android Market, BT alleges.
The other patents cover navigation systems (Google Maps is the culprit here), location-based information (infringed just about everywhere) and digital rights management (Android Market is fingered).
If BT is successful in court it could force Google and Android handset makers to pay royalties on each Android handset that’s in use. That’s a lot of devices — this summer, Google Mobile president Andy Rubin took to Twitter to announce that “there are now over 500,000 Android devices activated every day.”
Life Without Sudo
Interesting thoughts from Jon Stokes – In the Cloud, There is No Sudo:
I’m an admin now for three Google Apps for Business accounts, and I’ve had some headaches recently with all three of them. So far, all of my problems seem to have arisen from errors on Google’s end, and as I went ’round and ’round with support for Google, Postini, and Spanning Backup, I got a first-hand reminder of one of the major reasons why so many IT pros are reluctant to jump on the cloud: as the title of this post says, in the cloud there is no sudo. Or if there is a sudo, then you don’t know the password. This is one very good reason why people who are accustomed to being super-users can sometimes panic when faced with the prospect of a public cloud migration.
Going All-In on E-Books

Anne Eisenberg on textbooks Making Science Leap From the Page
Sounds promising, but textbooks publishers have done little to create innovative e-books. I think the digital-only approach is the right one – you can't be a print publisher and dabble in e-books. You're disrupting your core business - print books - and all of the infrastructure and human resources that have been accumulated for a century. True innovation and meaningful disruption will come not from an incumbent, but from a new entrant into e-book publishing.
WHEN a college textbook, “Principles of Biology,” comes out from the Nature Publishing Group in January, one place it won’t be is on the shelves of school bookstores.That’s because the book was designed to be digital-only. Students will pay not for a printed edition at a bookstore, but for permanent access on the Internet ($49).
And when they open the book on their laptops, tablets and smartphones, they will find other differences, too. True, the text is packed densely with definitions and diagrams — it is meant to teach college-level science, after all, and is from the publishers of the august journal Nature.
Still, this isn’t your usual technical tome. The pages have some pizazz: they are replete with punchy, interactive electronic features — from dynamic illustrations to short quizzes meant to involve students rather than letting them plod, glassy-eyed, from one section to the next. Audio and video clips are woven into the text.
Photo by www.edufiend.com - http://flic.kr/p/Q1Hui
Monday, December 19, 2011
Siri Plays the Piano!
Shared by Jim Dalrymple Siri plays the Yamaha Disklavier piano using AirPlay:
We’ve all seen some cool things that Siri can do, but this has to be the best so far. The guys at Yamaha got Siri to play piano.
Microsoft and RIM
Some more good stuff from Jean-Louis Gassée 2011: Shift Happens:
First on Microsoft –
The company also reorged its mobile business: Andy Lees, formerly President of its Windows Phone division just got benched. The sugar-coating is Andy keeps his President title, in “a new role working for me [Ballmer] on a time-critical opportunity focused on driving maximum impact in 2012 with Windows Phone and Windows 8”. Right.
Ballmer once predicted Windows Mobile would achieve 40% market share by 2012, Andy Lee pays the price for failing to achieve traction with Windows Phone: according to Gartner, Microsoft’s new mobile OS got 1.6% market share in Q2 2011.
… and then RIM
‘Amateur hour is over.’ This is what the company imprudently claimed when introducing its PlayBook tablet. It is an expensive failure ($485M written off last quarter) but RIM co-CEOs remain eerily bullish: ‘Just you wait…’ For next quarter’s new phones, for the new BlackBerry 10 OS (based on QNX), for a software update for the PlayBook…
Intel Versus ARM
Intel. The company just re-organized its mobile activities, merging four pre-existing groups into a single business unit. In a world where mobile devices are taking off while PC sales flag, Intel has effectively lost the new market to ARM. Even if, after years of broken promises, Intel finally produces a low-power x86 chip that meets the requirements of smartphones and tablets, it won’t be enough to take the market back from ARM.
Here’s why: The Cambridge company made two smart decisions. First, it didn’t fight Intel on its sacred PC ground; and, second, it licensed its designs rather than manufacture microprocessors. Now, ARM licensees are in the hundreds and a rich ecosystem of customizing extensions, design houses and silicon foundries has given the architecture a dominant and probably unassailable position in the Post-PC world.
Sunday, December 18, 2011
$0.99 WiFi Scanner for Mac OS on Mac App Store
WiFi Scanner for Mac OS is $0.99 on Mac App Store. No promo codes, links or coupons needed.
WiFi Scanner is an easy-to-use tool for designing, verifying, and troubleshooting WiFi coverage. The tool provides information such signal strength, noise, manufacturer name based on MAC address prefix of device (OUI), and AP channel assignments for WiFi access points.
WiFi Scanner can also be used a security tool for detecting unauthorized and rogue access points. The app includes an audio alert (beep) feature that is directly related to RSSI / access point signal strength. This feature can be used to track down devices by listening for beep frequency instead of watching app screen.
WiFi Scanner is a great tool for personal use and for IT professionals.
- WiFi Scanner is an 802.11 wireless scanner and connection manager for Snow Leopard and Lion.
- It can be used for wireless site surveys, wireless discovery, and to connect to wifi networks.
- Scans 802.11 a/b/g/n Scans both 2.4 GHz and 5 GHz bands. See first screen shot below, Channel 11 is in 2.4 GHz band and Channel 161 is in 5 GHz band.
- Has WiFi analyzer feature for tracking signal of WiFi connection and graph over time for troubleshooting or optimizing placement of access points.
- The tool reports signal strength in dBm and shows access point BSSID/MAC addresses.
- Sort any column
- Command click one or more rows of results to Copy/Paste rows of results into own documents
- Double click results row to view window with RSSI and graph.
- Audio beep in monitor window increases as RSSI increases for access point being tracked. This is very handy for rogue access point tracking.
- UDP listener for use with Sensor Pro remote GPS iPhone app.
Smartphones and the Mobile Web

Nielsen’s “State of the Media: The Mobile Media Report” provides a snapshot of the current mobile media landscape and audiences in the U.S. and highlights the potential power of mobile commerce in the near future.
...
Key findings From The Report:
- The majority of 25-34 and 18-24 year olds now own smartphones (64% and 53% respectively);
- The majority of smartphone owners (62%) have downloaded apps on their devices and games are the top application category used in the past 30 days;
- The number of smartphone subscribers using the mobile Internet has grown 45 percent since 2010;
- 87 percent of app downloaders (those who have downloaded an app in the past 30 days) have used deal-of-the-day websites like Groupon or Living Social;
- Younger groups text the most. In Q3, teens 13-17 sent and received the most text messages (an average of 3,417 each month).
- Posted using BlogPress from my iPad
Saturday, December 17, 2011
Feedback on Stanford Online Classes
Hernan Amiune is not so happy with Stanford's online classes - at least the end result.

Stanford Online Classes. Like A Great Movie With A Bad Ending:
Professors are AWESOME!
The exercises are AWESOME!
The classes are AWESOME!
But then they send you the Statement of Accomplishment. This was obviously done by engineers with no knowledge of public relations or marketing. And maybe under the pressure of Stanford (lawyers?) to clarify that this wasn't a Stanford class.
Before the course started they promised the Statement of Accomplishment as an incentive to get you in the course.
When they got a lot of users they said “You will receive a statement of accomplishment from the instructor, which will include information on how well you did and how your performance compared to other online students. Only students admitted to Stanford and enrolled in the regular course can receive credit or a grade, so this is not a Stanford certificate.”
At the end they send you a pdf file that says something like this:hey you didn’t complete any Stanford course, you were just part of an experiment and this is an automated message.
It’s a pity because the courses were so great, so tasty, but this leaves you with some bad taste in your mouth. And I think that not sending any Statement of Accomplishment would have been much better.
Friday, December 16, 2011
Password Security Is Broken
Password Security Is Broken, Say Experts:
Identity fraud is one of the biggest threats to unwary web users today. It can come in a variety of forms but is often the result of an online account being hacked or details phished via social engineering.
I recently met Jason Hart, former ethical hacker and now managing director of secure authentication firm Cryptocard, who has been banging on for years about how password-based approaches to account authentication are no longer sufficient.
Now, of course, he would say that, given that Cryptocard's job is to sell alternative two-factor-based authentication technology, whether it's via key fob token generators, or passcode-generating software which can be installed on a smartphone.
However, the sheer number of security breaches which have occurred because password security systems have been cracked in the most basic and simple way backs up the two-factor message.
"Why should a [hacker] go to the effort of finding a vulnerability when he could target the password?" Hart toldV3.
"The problem has always been there but the reliance of social networks and cloud computing [sites] on passwords has been explosive. Password security is the only thing that impacts confidentiality, integrity, availability, accountability and auditability."
A Power Shift at Google?
Brad McCarty reporting … Gundotra in, Mayer out. In Google's inner circle that is
TED Video: Sal Khan
Karl Kapp shares … Great TED Video by Salman Khan:
The man who created Khan Academy talks about education in this thought provoking video.
Siri Coming to non-iPhone4S?
Not just yet.
From Alex Heath – Apple Makes Siri iPhone 4 Port Legally Possible With Today’s iOS 5.0.1 Update:
Siri is by far the iPhone 4S’s most-desired feature, and many non-4S users have been clamoring for hackers to make the voice assistant available on older iOS devices. While Siri ports have been demoed to the public before, it’s been made clear that public distribution is not possible at this time due to legal issues.
Apple has made a Siri port legally possible with today’s iOS 5.0.1 revision by offering wide-open access to system files that were previously encrypted.
Thursday, December 15, 2011
U.S. Teens Triple Data Usage, But Texting Still Tops
Jay Donovan reporting … U.S. Teens Triple Data Usage:
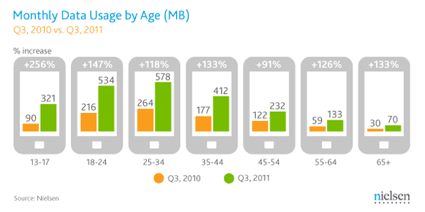
Nielsen is reporting today that teens have more than tripled mobile data consumption and also continue to hold top spot as the most engaged mobile messaging segment.
The report states that “In the third quarter of 2011, teens age 13-17 used an average of 320 MB of data per month on their phones, increasing 256 percent over last year and growing at a rate faster than any other age group”.
While this deluge of data consumption seems immense, messaging still remains the largest teen behavior in the mobile space, with the number of SMS/MMS messages reaching 3,417 per teen. Let me just say that again…3,417 texts per teen—seven messages per waking hour, according to the study. Um, WOW!
Congress Mulling Restrictions on Additional Unlicensed Spectrum
The spectrum bill that passed the House last night will make any technologist weep. I know the tech community is upset over the Stop Online Piracy Act (SOPA), but this bill represents a somewhat geekier threat–killing more unlicensed spectrum. So Silicon Valley may want to get active over this one too. The House version of the bill will ensure that none of the airwaves auctioned off from the digital TV band will be used for unlicensed wireless, where services such as Wi-Fi or white spaces broadband exist.
Free airwaves are good for innovation.
Unlicensed spectrum are the free airwaves that any company can use as long as the it meets certain FCC guidelines. The 2.4 gigahertz and 5 gigahertz bands that Wi-Fi currently works in are unlicensed, as are the 900 Mhz bands used by baby monitors and cordless phones. But under the bill passed last night, none of the megahertz the government gets back from TV broadcasters will be set aside for such use, and instead would end up getting auctioned off to licensed users, such as a network operator.
That’s bad for a variety of reasons, specifically because some of those bands are supposed to be used for delivering Super Wi-Fi or white spaces broadband.
Cannonball Versus a Tub Full of Mercury
Very cool video shared by Sean Michael Ragan
Dropping a Cannonball into a Tub Full of Mercury:
Continuing our “what happens when you drop stuff into stuff?” series is this short video segment from the BBC. As with dropping a magnet through a copper pipe, many of you probably know what to expect, here. But it’s nonetheless cool to see. Mercury is so beautiful; such a shame it’s also so toxic.
Wednesday, December 14, 2011
I Love Technology
Great use of GPS;)
Today, my husband changed the voice on my car's GPS to Mr T's. I don't know how to change it back. I've been saying, "I pity the fool" over and over again ever since.
Clay Johnson's The Information Diet
Clay Johnson's new book and an innovative way of engaging an audience – giving away the first chapter online. The Information Diet - first chapter released:
I've just put the first chapter of the Information Diet up on Scribd. Give it a look-see and tell me what you think. It's a great guide for what to expect from the book as a whole. And don't forget to pre-order yourhardcover so you can have the awesome, conversation-starting cover, or the kindle version today.
Tuesday, December 13, 2011
What Does it Take to be a Top 10 iOS App?
From Adrian Covert – It Takes 30,000 Downloads a DAY just to Crack the iOS App Store's Top 10:
If you think the whole mobile apps craze is just a fad, consider this statistic: any free app in the iOS App Store's top 10 list is receiving at least 30,000 downloads a day. A DAY! For the US alone!
Melted Fiber-Optics and a Large NYC Outage
If you follow our business really closely, you probably know that we had a pretty big outage in the East Village on October 6th. You sure know about it if you happen to live in New York City and have a Twitter account – it was understandably all over the place.The New York Times’ East Village blog mentioned this, naturally. Essentially, a number of nodes connected to this portion of fiber lost network connectivity, interrupting service to approximately 24,000 customers in the area.
Our VP of Engineering in New York City shared some photos of the mess with me, and I thought our customers would like to see what a large, lengthy, and unusual outage looks like.
...
Here, you can see a cross-section of what the cable looked like before the fire:
I took a closeup with the macro lens on my iPhone:
Those multicolored things are a protective sheath around a single fiber-otic strand roughly the width of a human hair. Each strand carries video, broadband, and phone services to a node, which, again, can serve 300-600 homes. The colored sheaths are slathered with a sort of insulating goo inside the cable shell to help protect the fiber from moisture. The whole enterprise looks a little like an alien cyborg’s reproductive organ, doesn’t it?
Here’s what the cable looked like after being subjected to an electrical fire:
And again, with an iPhone macro closeup:
The Cable Company Head End Explained
I discovered what an incredible feat of round-the-clock engineering it takes just to get cable, phone and broadband services to the house 24 hours a day, 7 days a week with minimal interruption. The sheer cost and infrastructure it takes to make it so people all over America can sit at home with their pants off and tweet about popular television programs is mind-boggling.
…
In this video Larry Pestana, our VP of Engineering for New York City, shows us what it takes to actually get television signals to your house from space through our “head end.”A “head end” is a plant that takes TV signals from satellites, processes them into cable quality and distributes them throughout a network and into homes.
Here’s a look at our head end at the 23rd Street facility in New York City – hope you enjoy it:
Head End: How Cable Gets to Your House from Space from Time Warner Cable on Vimeo.
Gifts for Makers
Sylvia's Super-Awesome Make Holiday Gift Guide 2011 - YouTube:
Read the full guide: http://wp.me/p1CIX9-vEc
Welcome to Sylvia's Super-Awesome Make Holiday Gift guide 2011! Your source for what to get your favorite maker this holiday season.
Is Google Wallet Secure?
As the first real payment system leveraging NFC on Android, Google Wallet is a very intriguing new consumer app for smartphones. But as we always ask: is Google Wallet secure?
This analysis provides a high-level review of the data transmitted and stored by Google Wallet, with the goal of determining if any sensitive data is at risk. Security vulnerabilities in Google Wallet, if they exist, could place the consumer at risk for financial or identity theft. The testing performed here is the basis for our appWatchdog review of Google Wallet.
I started the analysis on the initial release, however several updates were pushed out – and one security issue I had uncovered was addressed by an update. Ultimately I froze my analysis to Version: 1.0-R33v6 of Google Wallet.
Before I dive into the details, if you find our high level security analysis of Google Wallet interesting, you might find these related services and studies equally interesting:
- appSecure, viaForensics’ mobile app security service
- appWatchdog, our free mobile security and privacy service
- Mobile App Security Study, a free report on 100 popular mobile apps
- Mobile Security Risk Study, an 85 page report focusing on iPhone and Android in the Enterprise
…Summary of Google Wallet security findings
So, in summary, here are the items of note from my high level analysis. Bear in mind this is nowhere near the level of testing an app like this deserves but since this is done on our own time, it’s all I could manage thus far. Anyway, here goes:
- A fair amount of data is stored in various SQLite databases including credit card balance, limits, expiration date, name on card, transaction dates and locations and more.
- The name on the card, the expiration date, last 4 card digits and email account are all recoverable
- [Fixed in Version 1.1-R41v8] When transactions are deleted or Google Wallet is reset, the data is still recoverable.
- The Google Analytic tracking provides insights into the Google Wallet activity. While I know Google tracks what I do, it’s a little frustrating to find it scattered everywhere and perhaps in a way that can be intercepted on the wire (non-SSL GET request) or on the phone (logs, databases, etc.)
- [Fixed in Version 1.0-R33v6] The application created a recoverable image of my credit card which gave away a little more info than needed (name, expiration date and last 4 digits). While this is not enough to use a card, it’s likely enough to launch a social engineering attack.
While Google Wallet does a decent job securing your full credit cards numbers (it is not insecurely stored and a PIN is needed to access the cards to authorize payments), the amount of data that Google Wallet stores unencrypted on the device is significant (pretty much everything except the first 12 digits of your credit card). Many consumers would not find it acceptable if people knew their credit card balance or limits. Further, the ability to use this data in a social engineering attack against the consumer directly or a provider is pretty high. For example, if I know your name, when you’ve used your card recently, last 4 digits and expiration date, I’m pretty confident I could use the information to my advantage. When you add data that is generally available online (such as someone’s address), an attacker is well armed for a successful social engineer attack.
Three-Week Online Courses
Alvin Community College is offering students a chance to get a headstart on the spring semester with online courses beginning Dec. 19.
Courses being offered include Composition I and II, American National and State Government I and II, U.S. History to 1877, U.S. History since 1877, Texas History, Developmental Math - Intermediate Algebra, College Algebra, Fitness and Wellness, Introduction to Philosophy, General Psychology, Introductory Sociology and Interpersonal Communication, according to a press release.
Monday, December 12, 2011
How Easy is it to Copy a Captured Drone?
David Axe reports that It Won't Be Easy For Iran To Dissect, Copy U.S. Drone:
Prepare the dissection table. Iran says it’s planning to disassemble its prized acquisition: a CIA-operated drone that apparently crashed on its territory. Its goal: to learn how the drone, apparently a stealth RQ-170 Sentinel, evades radar and how its top-secret sensors work. Which has the U.S. worried about Iran copying its advanced flying robot. ”There is the potential for reverse engineering, clearly,” U.S. Air Force Chief Gen. Norton Schwartz conceded.
But Iran will probably need help from arms exporters Russia and China in breaking down the flying-wing unmanned aerial vehicle (UAV) — meaning the RQ-170′s secrets could ultimately fall into the hands of, well, pretty much every country with an interest in sticking it to Uncle Sam. Luckily for Washington, however, reverse-engineering a high-tech drone is easier said than done, according to two UAV designers who spoke to Danger Room on the condition we not print their names.
Isaac Newton’s Personal Notebooks Go Digital
Cambridge's site is a little uncooperative, but this is a very cool project.
Shared by Brandon Keim – Isaac Newton’s Personal Notebooks Go Digital:
The largest collection of Isaac Newton's papers has gone digital, committing to open-access posterity the works of one of history's greatest scientist.
Among the works shared online by the Cambridge Digital Library are Newton's own annotated copy of Principia Mathematica and the 'Waste Book,' the notebook in which a young Newton worked out the principles of calculus.
Other of his myriad accomplishments include the laws of gravity and motion, a theory of light -- pictured above are notes on optics -- and his construction of the first reflecting telescope.
Sunday, December 11, 2011
What's Going on With HP and WebOS?
Either she thinks we’re dimwits, or she’s being cleverly cheeky. Does she think we’ll fall for the tired corpospeak? “Victory! WhatWereWeThinking v3.0 has been released to the Open Source community”. Or is she slyly fessing up? “After much abuse inside the HP cage, it’s clear that webOS can only be restored to health if released into the wild.”
And regarding new CEO Meg Whitman ...
When I hear Whitman make such statements, I’m reminded of the old joke about the difference between a computer salesperson and a used-car salesman: The used-car gent knows he’s lying. For my alma mater’s sake, for HP’s good, let’s hope Meg Whitman knows she’s putting us on.
Is LTE Standardization a Problem?
Hopes of a cross-network LTE standard were dashed months ago, when Verizon confirmed its 4G band won't overlap with AT&T's. What we didn't realize, though, was just how globally fragmented this technology is likely to become. A report by Wireless Intelligence predicts there'll be 200 LTE networks around the world by 2015, running on as many as 38 different frequency combinations. Moreover, the most common 700-900MHz spectrum range could account for just 16 percent of these networks. This stands to make carrier locking and band incompatibility on handsets even bigger hassles than they are today.
Saturday, December 10, 2011
Verizon Lands High-Level Federal Security Certification
Robert Mullins reporting – Verizon Lands High-Level Federal Security Certification:
Verizon has earned "Level 3" certification by the U.S. government for its Universal Identity Services (UIS) identity and access management technology to protect computer networks. Verizon says it is the first identity access provider to reach Level 3 certification.There are four levels of certification under the federal Identity Credential and Access Management (ICAM) program, Tracy Hulver, chief security strategist for Verizon, explained. The lowest level is Level 1, in which a user identifies him-or-herself as who they say they are and no further identification is needed. Level 2 certification matches the person’s name with some identifying information such as their address or the last four digits of their Social Security Number. Level 3 adds an additional layer of vetting called second-factor authentication.
With Verizon’s UIS product, a user enters their name and perhaps an ID number but then also is given an “online antecedent,” Hulver said, which could be a list of questions the person has to answer in a given amount of time. For example, the person could be shown a list of addresses and be asked which of them is not an address at which they have ever lived. The vetting could include a number of such questions.
“The more questions you answer within the time frame, the higher the level of probability that you are who you say you are,” Hulver said. Level 4 is the highest level of authentication and also requires a third factor such as a smart card with a biometric identifier attached to it; Hulver called Level 4 “the equivalent of a notary certification.”
Friday, December 09, 2011
Turn an iPad Into an Oscilloscope
Imagine replacing these …

with these …

From Brian McLaughlin – Oscilloscope Turns iPad Into a Serious Science Tool:
[The] iMSO-104 oscilloscope. What makes this scope so different? It is a very small module, smaller than the Arduino Uno sitting next to it on my desk, that plugs into your iOS device and your iOS device handles all of the display and heavy duty work for the oscilloscope! I usually have my iPad or iPhone with me when I am working so this seemed like an ideal solution. I was rather reserved about my expectations. I had used some awesome high-end scopes at work and I wasn’t sure how this would stand up to my expectations. I have to say, I am impressed.
...
I really didn’t mean to write such a glowing review but I have to say that I am very impressed with this scope. There are only a couple of things I would say could use improvement. The zoom function, as I mentioned above, works with the normal iOS finger swipes but sometimes you may inadvertently change a scale you didn’t mean to change if you aren’t pinching close enough to horizontal or vertical on the display. This got me a couple of times. There is also the location of the trigger point. A quick button on the scope to recenter this marker when you zoom would be a useful feature. Those are the only two real issues I found in my operations and I did a great deal of exploring. The amazing thing is that those and many other enhancements are fixed with software updates to the iOS app. You can check out the app itself for free and take the interface for a spin. It has a demo mode that lets you see what the scope can do.
The Oscium iMSO-104 is available directly from the Oscium website as well as a few other retailers such as ThinkGeek for $299.99. Oscium also makes an iOS-enabled RF Power Meter, Spectrum Analyzer, and combined Power Meter/Spectrum analyzer. I love this idea of using iOS devices to drive instrumentation!
Oscilloscope photo via realblades
802.11ac - 1.3 Gbps Throughput!
Gigabit-speed wireless LAN products based on the emerging IEEE 802.11ac standard will start shipping next year and usher Wi-Fi into its next era of high speed and long range, communications chip maker Broadcom said Thursday.
The new technology will use beam-forming, wide bands and multiple antennas to deliver as much as 1.3G bps (bits per second) of real-world throughput, with a longer range and better wall-penetration capability that will help it serve entire homes, said Rahul Patel, vice president of Broadcom's mobile and wireless group. It represents a big step up from 802.11n, the current standard that typically tops out at about 300M bps, he said.
Consumers will need faster Wi-Fi soon to enjoy activities such as sending multiple streams of video to a TV, Patel said.
Thursday, December 08, 2011
Happy Birthday Coax!
1931: The new invention of the coaxial cable is issued a U.S. patent, which will eventually deliver the gift of ubiquitous telephony and cable television.
- Posted using BlogPress from my iPhone
Wednesday, December 07, 2011
An iMac with HDTV?
From John Paczkowski – Apple May Use iMac Refresh as Step Toward Apple Television:
Here’s a novel theory: The Internet-connected HDTV that Apple is rumored to have in the pipeline will be preceded by another device, which will pave the way for it:
A new iMac with integrated TV functionality.
That’s the latest speculation from Wedge Partners analyst Brian Blair, who believes there will be a step between the Apple TV and the Apple Television.
“We believe Apple’s redesign of the iMac in the first half of 2012 will likely usher in some … TV capability into the iMac offering first, effectively taking the high end and larger screens of the iMac line and pushing it toward the TV market by integrating Apple TV and iCloud features into a slimmer all-in-one PC,” Blair writes. “Apple could effectively start with what they already have on the manufacturing line and slowly push their offering from 27 inches and scale up from there to 32 inches and then move on to the 42, 50 and 55 inch market.”
Autodesk and iOS
From Daniel Eran Dilger Autodesk discovers new consumer market via iOS apps:
Thanks to Apple's iOS App Store, Autodesk has attracted more new customers than it has ever had across its previous 29 years in business, transforming the company and causing it to launch a new consumers products division.
A profile of Autodesk's shift toward consumers, published by MIT's Technology Review, highlights how the company's experimental SketchBook for iPhone and iPad has given the company, best known for its professional, high end AutoCAD software, an entirely new market.
In 2008, Autodesk was developing SketchBook as a consumer product for PCs, but the product didn't attract much attention. Chris Cheung and Thomas Heermann, two middle managers, began exploring the idea of porting the paint and sketch app to the new iPhone App Store.
After launching the $2 iPhone app in September of 2008, the pair hoped for 100,000 downloads over the next year. Instead, they hit a million downloads in 50 days. The company released a $5 iPad version that launched alongside the tablet in April 2010.
After roughly 7 million app downloads, Autodesk's SketchBook and the estimated $15 million in revenue the app has generated isn't rivaling the company's high end software revenues that total $2 billion.
Tuesday, December 06, 2011
Researcher Demos Potential Smartphone Botnets
Sean Gallagher reporting – Researcher demos threat of "transparent" smartphone botnets:
In a presentation at TakeDownCon in Las Vegas today, security researcher Georgia Weidman demonstrated how malware on smartphones could be used to create smartphone "botnets" that could be used in the same way as PC botnets, providing hackers with a way to insert code between the operating system's security layers and the cell network. In an interview with Ars Technica, Weidman said that the approaches used by Carrier IQ developers to create phone monitoring software could be adopted by hackers as well to create botnets that could silently steal users' data, or send data without users' knowledge. "From what I've seen in Carrier IQ, they just didn't think about what they were going to do," Weidman said. "But malware writers are going to take advantage of those techniques.
Increase Productivity by Decreasing Network Bandwidth
An interesting, but somewhat counter-intuitive approach to productivity from Clay Johnson – Slow your Bandwidth to Increase your Focus:
My super secret weapon in writing The Information Diet was that I could afford to take a month off, go into seclusion, and get this book done. Few frameworks I can offer can afford you the freedom from distraction that I got working from inside a remote cabin off of coastal Georgia. The most important thing I had there wasn't scenery -- mosquitoes ate me alive every time I went outside -- it was the miracle of slow bandwidth.
Facebook's Lack of Privacy Bite's Mark Zuckerberg
Irony!
Shared by Ben Brooks How to View Private Facebook Photos:
So glad I am not on Facebook. Also here are Mark Zuckerberg’s private photos.
Google Adds Graphing to Search
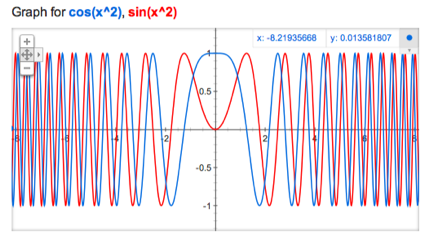
Google has added graphing functionality to its seemingly ever-growing list of search bar capabilities, the company announced Monday in a blog post.
Now, when users type in a function — for example: sin(x) — the first search result will be an interactive graph allowing users to explore different related values for x and y.
Users can also plot multiple functions by separating them with commas. The new feature is available in most browsers and “covers an extensive range of single variable functions including trigonometric, exponential, logarithmic and their compositions,” writes Google engineer Adi Avidor.
3.2 Million Dots; 210 Hours
Shared by Deron Bauman – Miguel Endara, Hero:
Watch as Miguel Endara draws a portrait of his father by meticulously tapping out millions and millions of dots. Like 2 Years & +200,000 Jelly Beans, this really made me itch.
Monday, December 05, 2011
6 Hot IT Jobs for 2012
Despite ominous predictions about how cloud computing will eviscerate IT departments, 2012 is shaping up to be a great year for IT careers. Cloud computing is in fact creating new roles for IT professionals, while the proliferation of smartphones and tablets has ignited demand for software developers. The IT job market, which experienced a strong rebound in 2011 after the recession, is expected to burn even brighter in 2012, despite global economic challenges, according to IT staffing industry executives.
"I expect it to be better and not just a little bit better," says Tammy Browning, senior vice president of Yoh staffing's western region. "I would say it will be 10 to 15 percent better than 2011 in terms of hiring."
Indeed, Jerry Irvine, CIO of Chicago-based IT outsourcer Prescient Solutions, says he has hired 30 people so far in 2011 and plans to add another 30 to 40 next year. Currently, he has 13 open positions for senior project managers, SharePoint programmers, infrastructure engineers, systems engineers and ITIL helpdesk technicians.
Aggressive hiring is good news for the many IT professionals seeking new jobs. According to the latest IT Employee Confidence Index from staffing firm Technisource, 32 percent of 257 employed IT professionals plan to look for a new job.
IT staffing experts also anticipate that IT salaries will finally spike after years of stagnation, as employers realize they need to pay premiums for certain IT skills in a competitive job market.
...
Here are the six IT jobs that staffing experts say will be in greatest demand and will command the highest salaries in 2012. The best part: Many of these jobs are also serious fun.
1. Mobile Application Developers
2. Software Developers
3. User Experience Designers
4. IT Security Professionals
5. Data Warehouse Architects, Analysts and Developers
6. Infrastructure Professionals
Sunday, December 04, 2011
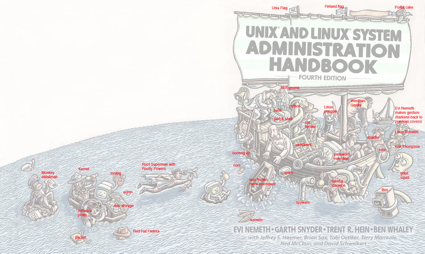
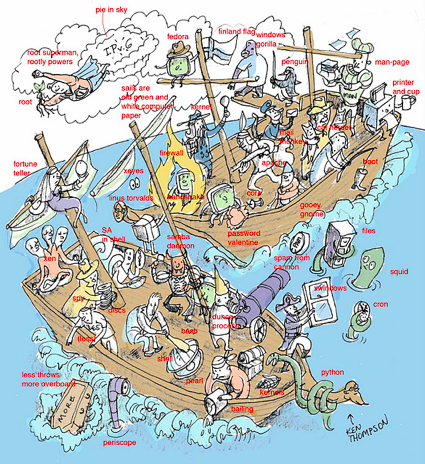
Unix and Linux System Administration Handbook
From Lisa Haney … The meaning behind the cover of "Unix and Linux System Administration Handbook":
I was asked by a few people to explain the image on the cover of the "Unix and Linux System Administration Handbook (fourth edition)", so I'm posting this explanatory version... some of it will make no sense unless you look at the interior cartoons (like the Windows Gorilla), but I assumed anyone who really cared probably owned it, and would get these references. I also include the initial sketch, so you can see what ideas were nixed by the authors, and what was added...
When Will Batteries Get Better?
Moore's law has provided us with dramatic improvements in CPUs, memory, hard disks, etc, but has had little impact on batteries. While the iPad has great battery life, this is due mostly to being almost all battery internally.
Louis Bergeron reporting … Stanford develops new batteries:
Stanford researchers have used nanoparticles of a copper compound to develop a high-power battery electrode that is so inexpensive to make, so efficient and so durable that it could be used to build batteries big enough for economical large-scale energy storage on the electrical grid – something researchers have sought for years.
CyberMonday and the Digital Divide
From Susan P. Crawford – Internet Access and the New Divide:
FOR the second year in a row, the Monday after Thanksgiving — so-called Cyber Monday, when online retailers offer discounts to lure holiday shoppers — was the biggest sales day of the year, totaling some $1.25 billion and overwhelming the sales figures racked up by brick-and-mortar stores three days before, on Black Friday, the former perennial record-holder.
Such numbers may seem proof that America is, indeed, online. But they mask an emerging division, one that has worrisome implications for our economy and society. Increasingly, we are a country in which only the urban and suburban well-off have truly high-speed Internet access, while the rest — the poor and the working class — either cannot afford access or use restricted wireless access as their only connection to the Internet. As our jobs, entertainment, politics and even health care move online, millions are at risk of being left behind.
Saturday, December 03, 2011
Kill the Penny - The Case Against Pennies
C.G.P. Grey with a really well-done video makes a strong case for doing away with the penny.
Friday, December 02, 2011
RIM Loses $485 M in Unsold PlayBooks
Research in Motion announced on Friday that its inability to sell PlayBook tablets to consumers has forced the company to take a $485 million charge.
The mostly non-cash inventory provision is yet another bad sign for the PlayBook, which has failed to gain any traction in the tablet market dominated by Apple. Retailers began a fire sale of the touchscreen device last month, slashing as much as $300 off the price of the PlayBook in an effort to move inventory.
The PlayBook sold just a half-million units in the first quarter of availability, but dropped to 250,000 the following quarter. In the third quarter, sales dipped to just 150,000.
What to do About Carrier IQ on Your Phone
Carrier IQ, the rootkit that can log everything you do on your phone, is easy to turn off on the iPhone and we noted yesterday how to check and remove Carrier IQ on Androidusing an app from the developer who discovered the Carrier IQ scandal, but that method required rooting your phone. Voodoo Carrier IQ Detector is a free app available on Android Market that can check for—but not yet remove—the spying software. It's easy to install and you don't need your phone to be rooted.
Verizon Gets More Spectrum to Expand LTE/4G
Verizon has a pretty serious head start in the LTE race. To make sure it stays at the front of the pack, Big Red has entered an agreement with SpectrumCo (a joint venture between Comcast, Time Warner and Bright House) that sees 122 AWS spectrum licenses transferred to the carrier for $3.6 billion and some commercial agreements. The deal will allow the companies to become authorized retailers for each others products, eventually giving the cable companies the ability to offer Verizon Wireless service as wholesalers. For its part, the House that Droid Built scores a boat load of new spectrum that may become crucial in expanding its network and ensuring that speeds don't drop off significantly as more customers transition to 4G.
Netspot – Free WiFi Site Survey Tool for Mac
Great tip and video from Alan Henry!
Netspot for Mac Makes Diagnosing Wi-Fi Signal Problems Quick, Easy, and Free:
Everyone has decent Wi-Fi signal when they're sitting in the same room as their wireless router, but what about across the apartment, or in the basement? If you think you should have signal but don't, free site survey app Netspot is a utility that gives you the tools to draw out your floorplan, walk about your home or office with your laptop, and survey network strength, available networks, and channels in use along the way.
The app starts you off with a drawing tool where you can lay out the floorplan of your home or office. Once you've given it a rough idea of how your space is laid out, you can click any spot on the map to have the app scan the area for available wireless networks, their network type, the signal strength for each network, and more. The app will save the information behind the scenes, and you can move on to the next spot in your space to test. After you've covered the whole area, Netspot will show you where your wireless signal is the strongest, where it seems to drop off, and even give you a color-coded heatmap of your space so you can see where signal is the strongest and where you may need to install a repeater for a little signal boost.
Netspot is pretty powerful for a free utility, and gives you a great deal of information about the wireless networks in your area that you can use to decide which channel your network should be on and where you should position your wireless router. Best of all, it's completely free.
Fortran is Back!
Times to dust off my old programming chops ...
James Reinders reports that Fortran is more popular than ever; Intel makes it FAST – Blogs - Intel® Software Network:
Just this past week, a senior radio telescope astronomer told me about the shift from C++ back to Fortran in his corner of the world. It is all about efficiency. He believes this is a trend that will get stronger as we head to ExaFLOP scale machines at the end of this decade.I'm sure C++ has nothing to fear, but neither does Fortran.
As far as we can tell, there are more Fortran programmers today than ever. Fortran is almost certainly a smaller % of the market than ten years ago but numerically it has grown. This is because the Fortran population is not growing nearly as fast as programming in general. But it is an important piece of the pie.
And judging by the growth of science and high performance computing, this will continue.
Intel Fortran compilers are leading the way in performance, features and support for new standards.
What's Fortran good for? From Bridget Moore's interview of Steve Lionel on Why Fortran Matters.:
Q: What applications are best written in Fortran?
S.L.: For something like string processing, Fortran would not be my first choice. But if you’re doing number crunching, working with a lot of floating-point data, or doing parallel processing, it’s an excellent choice. Its strengths in array operations -- its wide variety of routines -- make it attractive, and there is a huge library of freely available high-performance routines written over 40 years that still work together.
Thursday, December 01, 2011
Are Mobile Developers All Millionaires?
Ziggy, Android game developer, shares his Android game income stats – November
Ad revenue from free apps:

... just under $500 since April. And paid apps?
Paid Games
I sold 2 copies of Bus Jumper in October, and I actually sold my first copy of Drippy. Exciting times! I’ll get $2.02 from Google one of these days.
- Posted using BlogPress from my iPad
What's the Hottest Major on Campus?
Carolyn Duffy Marsan reporting - Computer Science is the Hottest Major on Campus
The nation's best undergraduate computer science programs are bracing for a record number of applications this fall, as more high school seniors are lured by plentiful jobs, six-figure starting salaries and a hipster image fostered by the likes of Steve Jobs and Mark Zuckerberg.
Early admissions are piling up at elite tech schools, including Carnegie Mellon University, Harvey Mudd College and Rose-Hulman Institute of Technology - all of whose undergraduate computer science and engineering programs are rated tops by U.S. News & World Report, the de facto college ranking in the United States.
- Posted using BlogPress from my iPad
Marriott Hacks a Hacker
A single security breach costs between $400k and $1m - wow!
From John Leyden – Hacker Cuffed In Job Interview Sting With Hotel He Blackmailed:
A job-seeking Hungarian hacker has pleaded guilty to breaking into the systems of the Marriott hotel chain before attempting to blackmail his way into an IT job.
Attila Nemeth, 26, sent Trojan-infected emails to Marriott employees late last year, according to his plea agreement, in a move that successfully allowed him to extract confidential and financially sensitive information from the hotel chain's network. He then apparently threatened to reveal this information unless he was given a job maintaining Marriott's systems.
Marriott reported the approach to the US Secret Service, which set up a sting operation. An agent posed as a Marriott human resources worker, entering into email and phone conversations with Nemeth, ostensibly about the possibility of a job.
Nemeth agreed to travel to the US in January, supposedly for a job interview, after accepting a plane ticket bought at Marriott's expense. According to his plea agreement, during the "interview", Nemeth was coaxed into revealing how he broke in Marriott's systems and the level of confidential access he'd obtained. He also admitted sending the malware-loaded emails. He was subsequently arrested and charged with computer hacking and threatening to expose confidential information offences, the Wall Street Journal reports.
The Marriott estimates spending between $400,000 and $1m in consultant fees and others costs dealing with the security breach and figuring out what damage Nemeth might have caused.
Unity and Ubuntu's Fall
From Jason Kennedy Ubuntu: Wake up and smell the Unity against you:
In the past few months, Ubuntu seems to have experienced a serious drop in popularity. It can be said that Linux distributions rise and fall when something new becomes the latest and greatest, but this turnaround seems sudden and could possibly be due to some recent design changes on Canonical’s part.
Canonical switched Ubuntu over to the Unity user interface, and a correlation seems to have occurred between this and a slump in its usage numbers. Royal Pingdom has recently compiled data from DistroWatch which seems to confirm what many have been saying about Ubuntu’s popularity: The number of hits to DistroWatch’s Ubuntu page is down 47% over the last 30 days, where Mint is up 105%. Note that the statistics are based on the normal amount of traffic for 2010, and that DistroWatch itself has doubled in size this year. What it means is that overall there’s been a decline in users searching for Ubuntu Linux, and also a huge rise in those users searching for Linux Mint.
Design: From Napkin to Patent
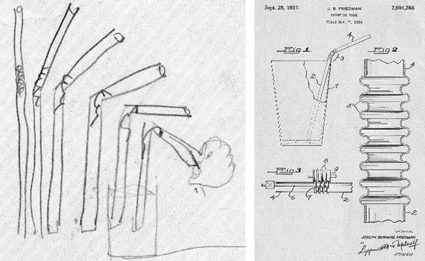
My daughter loves bendy straws!
Origins of the Bendy Straw: From Napkin to Patent:
If, like me, you’re a fan of Henry Petrowski’s book The Evolution of Useful Things, or are interested in the history of technology in general, you will probably enjoy Derek Thompson’s quick biography of the ubiquitous plastic drinking straw over at The Atlantic:
Here is a short history of the drinking straw in 30 seconds. Historians don’t know what civilization first came up with the idea of sticking tubes into cups and slurpling, but the earliest evidence of straws comes from a seal found in a Sumerian tomb dated 3,000 B.C. It shows two men using what appear to be straws taking beer from a jar. In the same tomb, archeologists also found history’s first known straw — a tube made from gold and the precious blue stone lapis lazuli.
It’s unlikely that Sumerians created the ur-straw all by themselves. The metal straw Argentinians use to drink mate (sometimes called a bombilla) is known be centuries old, at least. In the 1800s, when the rye grass straw came into vogue, its virtues — cheapness and softness — were also its vices, as it had a tendency to come apart in liquid. There have been two major straw innovations in the last 150 years.
#1 U.S. University for Startups?
Not Stanford or MIT, but University of Utah!
The #1 University in the U.S. for spinning off startups may surprise you:
With roughly one-third the budget of MIT, the University of Utah was named the number 1 school in the U.S. for creating startup companies. It’s the second year in a row that the University claimed the top spot.
Wednesday, November 30, 2011
Vending Machine Fail
Wonder if the "remote desktop" or "messenger" apps work!



- Posted using BlogPress from my iPad
Are Open-Source Skills the Key for Finding a Job?
Open-source skills best hope for landing a good job:
In the midst of a weakening global economy and rampant uncertainty as to when the recession will lift from North America and Western Europe, one thing is certain: open-source technology skills may be the best hope for landing a good job. As reported by The Wall Street Journal, open source claims five of the top 10 keywords in Indeed.com's job listings, with Hadoop, Puppet, Android, and jQuery making the list, along with HTML5, a proxy for various open-source projects like ext-JS, SproutCore, etc.
But before you rip up your Microsoft Certified IT Professional certification, it pays to balance rising trends against dominant technologies.
Using Indeed.com, it's clear to see that interest in open technologies such as Drupal, Hadoop, and jQuery is exploding:
android,ubuntu,jquery,hadoop,drupal Job Trends Android jobs - Ubuntu jobs - Jquery jobs - Hadoop jobsDrupal jobs However, the picture becomes a bit murkier when you start adding in search terms like Microsoft's SharePoint:
android,ubuntu,jquery,hadoop,drupal,sharepoint Job Trends Android jobs - Ubuntu jobs - Jquery jobs - Hadoop jobs -Drupal jobs - Sharepoint jobs And gets even worse when throwing in "Oracle", ".Net", and "Windows":









