Although unscientific, some interesting data from Carson McDonald … #2012:
The following information represents all responses for the #code2012 tag on twitter that was started by @deadprogram. Compare to last years: #code2011
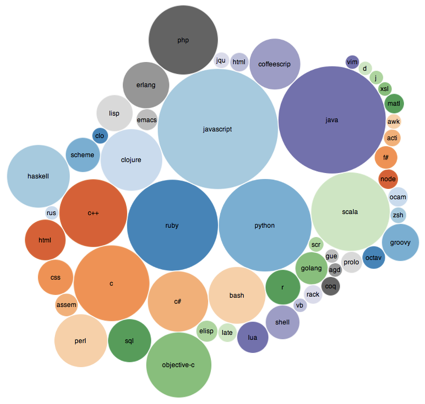
Mike Qaissaunee, a Professor of Engineering and Technology at Brookdale Community College in Lincroft, New Jersey, shares his experiences and perspectives on integrating new technologies in and approaches to teaching and learning. ~ Subscribe to this Blog
Although unscientific, some interesting data from Carson McDonald … #2012:
The following information represents all responses for the #code2012 tag on twitter that was started by @deadprogram. Compare to last years: #code2011

From John Callaham … Irony alert: Microsoft Office skills needed for some of Google's jobs:
Earlier this week, we reported that Google's Amit Singh, the head of their Enterprise division, believes that the company can get 90 percent of the businesses that use Microsoft Office to start using their own Google Apps products for their productivity software needs. It's an ambitious goal, but before they achieve it, they might start looking into hiring people in their own company that have skills in Google Apps.
As GeekWire.com points out, Google has a number of currently open job positions that require people to have some experience in using various Microsoft Office software. Just one example is listed on Google's job website for a new Insights and Innovation Analyst in the Partner Solutions division. Under "preferred qualifications", the job listing states:
3 years experience analyzing large data sets; proficient with analytical and presentation tools, including Excel (mastering pivot tables, graphs, and functions) and PowerPoint.
From Kenneth Thomas … Facebook paid 0.3% Taxes on $1.34 Billion profits:
If you are as cynical as I am, I know you are not surprised that Facebook paid Irish taxes (via Tax Justice Network) of about $4.64 million on its entire non-US profits of $1.344 billion for 2011.* This 0.3% tax rate is a bit below the normal, already low, Irish corporate income tax of 12.5%.
As with Apple, Facebook funnels its foreign profits into its Irish subsidiary.
Interesting stuff from Benjamin Kerensa ... The Shocking Truth About Wireless Coverage Maps
Awhile back I blogged about some excellent crowdsourced coverage maps available to customers of major wireless carriers and today I put together this infographic on the state of coverage maps provided by the carriers AT&T, Sprint, T-Mobile and Verizon. The inaccuracy of coverage maps does not just exist with major carriers but it’s also a problem with smaller carriers too.

- Posted using BlogPress from my iPad
Good list from Rich Hein … 9 IT Career Resolutions for 2013:
here's our list of nine career-related resolutions to make for 2013.
1. Work Better to Understand My Industry
2. Build a Career Map
3. Update Your Resume
4. Build a Personal Website for Your Brand
5. Create or Refine Your Social Profiles
6. Build a Social Network
7. Improve Your Follow-Up Skills
8. Personalize Your Cover Letters
9. Expand Your Horizons

Some great info from Raphael Mudge … How to Milk a Comp Sci Education for Offensive Security Skills:
Recently, a poster on reddit asked how to get into offensive security as a student studying Computer Science. Before the post was removed, the poster expressed an interest in penetration testing or reverse engineering.
I studied Computer Science at different schools (BSc/MSc/Whateverz). This is timely as a new semester is about to begin and students still have an opportunity to change their schedules if needed.
Offensive security is multi-disciplinary and people come into it with different backgrounds. Any background you master will equip you to become a useful contributor. Studying Computer Science (or even having a degree in the first place) are not the only path into this niche of security.
If you want to milk your Computer Science education for offensive security skills, here are my tips.
...
You should learn to program in a systems language, a managed language, and a scripting language. Learn at least one computer architecture really well too.
...
Python and Ruby are the preferred scripting languages in the security community. I lean towards emphasizing Python over Ruby. There are a lot of great libraries and books [1, 2] on doing security stuff with Python.
If you want to tinker with the Metasploit Framework, your best bet is Ruby. Ultimately–pick a project and use that as an excuse to master a language or tool. This is how you will acquire any skill you want (during and after college).
...
Take an operating systems course and the advanced OS course if you can. Usually these courses require you to work in a kernel and do a lot of C programming. Knowing how to work in a kernel will make you a better programmer and teach you to manipulate a system at the lowest levels if you need to.
After a good first course in operating systems, you will know how to program user-level programs, understand which services the OS provides you, and ideally you will have modified or extended a kernel in a simple way.
Take a compiler construction course to follow up with an architecture course. By the time you get through architecture and compiler construction, you will know assembly language for a specific architecture and how to use a debugger really well.
...
Active Directory administration, configuring Cisco routers and firewalls, using hacking tools, and other practical system administration skills are not usually covered in a CS curriculum. Be ready for this. If this is what you want, there are some good programs on Systems Administration and you may want to consider a switch.
...
If you get through the foundational material and find yourself hungry for more, try to arrange an independent study. I like independent study. It’s a chance for you to work on your own and produce something to prove you’ve acquired a skill or mastered a process. If your independent study produces open source or a useful paper, you may find the independent study boosts your career more than an academic transcript ever will.
...
Since you’re interested in offensive security, here are my two suggestions:
NYU Poly offers an Application Security and Vulnerability Analysis course. All of the lectures, homework, and project materials are available on the website. If you want to learn how to find vulnerabilities and write exploits, you could work through this course at an accelerated pace and spend the rest of the semester on a final project.
Syracuse University publishes the Instruction Laboratories for Security Education (SEED). This collection contains guided labs to explore software, web application, and network protocol vulnerabilities.
SEED also has open-ended implementation labs to add security features to the Minix and Linux kernels. If you ever wanted to write a VPN, develop your own firewall, or try a new security concept–these labs are a great start and any one of them could seed an independent study project. These labs were designed to provide a challenging end of course project. Two of these would make a very interesting semester of independent study.
Photo by sfslim - http://flic.kr/p/9xwiyQ
Handbook of Applied Cryptography
CRC Press has generously given us permission to make all chapters available for free download.
- Posted using BlogPress from my iPhone
Some interesting thoughts from Steve Kovach … It's Becoming Abundantly Clear That Google Doesn't Want To Share Android Anymore:
Now we have a report from the Wall Street Journal that says Motorola and Google are working together on a new smartphone that will launch next year. The so-called "X Phone" project will be completely separate from the Droid phones Motorola makes for Verizon.
...
The move marks a big shift for Google. After denying it intends to get into the hardware business, Google appears to be doing exactly that by using its own hardware company to develop a new smartphone to its exact specifications.
This should also scare the pants off Samsung, HTC, LG, and others that rely on the free, open-sourced Android operating system to make phones that compete with Apple's iPhone. If Google and Motorola make their own phone together, they're instantly turning other hardware manufacturers into competitors, not partners.
And what's to keep Google from restricting the use of Android from its competitors, leaving the latest and greatest software features for its own hardware built by Motorola?

Really fascinating stuff! Neal Ungerleider …How America's Spies Use iPhones And iPads:
Years ago, when spooks and government employees needed a secure smartphone, they turned to Research in Motion's BlackBerry. Times have changed, however. More and more government agencies are capitulating to the fact that their employees prefer Androids and iPhones. Even the National Security Agency (NSA) has adopted to changing times. Fast Company recently discovered that a copy of the NSA's security guidelines for iOS devices (PDF) is online and publicly available.
The unclassified NSA document, written by the Mitigations Group of the Information Assurance Directorate, is intended as a security recommendation manual for network administrators in the government and law enforcement sectors. Although most of it is written in a mixture of bureaucratese and dry technical manual styles, it provides valuable insight into iPhone and iPad spy capabilities and what the ubiquitous devices can do.
NSA employees are specifically worried about iPhones being hacked and converted into intelligence-gathering devices. A long section on risk mitigation warns on outsiders turning on “hot mikes” inside phones, of remote camera activation, of GPS location data being used to spy on users, and for spoofing credentials. While the NSA notes that iPhones are less susceptible to Bluetooth attacks than other smartphones, they are susceptible to exploitation via email spam and cellular networks.
While most of the NSA document reads like a standard best practices checklist, one thing stands out. The NSA seems to feel that human behavior on the part of an iPhone user is the biggest security liability--and endless suggestions are offered to mitigate the risk. One of the biggest risks for iPhones, according to the documents, is being plugged into an unsecured outlet for recharging. Security experts such as Brian Krebs have warned of the (possibly hypothetical) risk of "juice jacking"--rogue charging kiosks at airports or conventions secretly copying data from a victim's phone. As a precaution, the document recommends “provid[ing] additional AC outlet chargers” to users.
Photo by DonkeyHotey - http://flic.kr/p/9PCvvc
So what is a hybrid cloud? According to What Is:
A hybrid cloud is a composition of at least one private cloud and at least one public cloud. A hybrid cloud is typically offered in one of two ways: a vendor has a private cloud and forms a partnership with a public cloud provider, or a public cloud provider forms a partnership with a vendor that provides private cloud platforms.
Top Five Cloud Predictions from Greg Ness:
1) Hybrid cloud will enter the hype cycle as enterprises cross the process chasm between private and public clouds and data centers.
2) Amazon will experience intense pricing and functionality competition and hybrid cloud leadership will be up for grabs.
3) Retail colocation players who do not embrace hybrid cloud operating models will face margin pressures and will cede market leadership to those who do embrace and thrive on hybrid cloud.
4) Debates about public versus private cloud will be rendered meaningless.
5) There will be a flood of hybrid cloud startups and extreme “hybrid cloud” makeovers.
Great advice from Neil Joglekar … Tricks to better public speaking:
1. Don’t give a presentation - have a conversation
2. Speak in your voice and style
3. Tell personal stories

The Grammarist on Red Tape ...
In modern usage, red tape refers to the inefficient bureaucratic rules and procedures that prevent timely action. The figurative idiom comes from the old practice within governments, including the British one, of bundling official documents and bounding them with red tape, ribbon, rope, or string. The practice dates to the 16th or 17th century, and the figurative expression is nearly as old. The earliest instance cited in the Oxford English Dictionary is from 1736, but it was not common until the middle 19th century.
- Posted using BlogPress from my iPadPhoto by preservationgal - http://flic.kr/p/3JqcAL

Emil Protalinski ... Samsung Exploit Could Give Android malware Access to User Data:
The brilliant minds at XDA Developers have done it again; this time, a user by the name of alephzain claims to have discovered a vulnerability in multiple Samsung devices that gives access to all physical memory. The potential is huge: attackers could use malicious apps to wipe data and brick devices or, more likely, quietly access user data.
Photo by Darcy McCarty - http://flic.kr/p/5Md5c

Dylan Leckie ... Celebrating The Transistor and Disruptive Naval Research
On Dec. 16, 1947, while most Americans were preparing for the Christmas holiday, three physicists were locked in their laboratory, hunched over a work bench, constructing a peculiar gadget that would forever change the world. The transistor — the Bell Laboratories invention built by John Bardeen, Walter Brattain and William Shockley — would become ubiquitous in the future world.
Since its invention those many years ago, investments made by the Office of Naval Research (ONR) have extended and improved the transistor technology developed by Bell Labs. This month, which marks the 65th anniversary of the first transistor, ONR officials remember the invention and are reflecting upon the organization’s contributions to the evolution of the transistor — a technology regarded by many as the most significant scientific development of the 20th century.
Photo by Bob Jagendorf - http://flic.kr/p/buiT3W
- Posted using BlogPress from my iPad

From Jonathan Wylie ... An Educator’s Guide to AirPlay on iPads and Macs
AirPlay is a technology that Apple baked into their more recent devices to allow them to wirelessly mirror the content of one screen to another. This content can be music, movies, or other multimedia content. A teacher, for instance, can use AirPlay to wirelessly present their lesson to a class or demonstrate an app, while students could use it to share their work with their peers.
Photo by Kimb0lene - http://flic.kr/p/8VoPLH- Posted using BlogPress from my iPad
... but streaming video not encrypted. Hmmm ... could lead to a false sense of privacy. From Martin Sauter ... Observation: Youtube Is Now HTTPS - But The Streams Are Not
When I watched a video on Youtube today I noticed that the page's URL was https://www.youtube.com.... Interesting, I thought, it's encrypted now! If the streams are encrytped too, that would have interesting implications for video caching and compression servers in some mobile networks as they would no longer be able to compress and scale videos.
So I ran a quick Wireshark trace to see if the streams themselves were encrypted, too. However, they were not. An interesting implication of this is that the user might get the impression that the session is secure. But as the videos are sent in the clear, it's actually not secure at all. From the outside, it is no longer possible to see what the user is searching for, but which videos are streamed are still visible and can be cached or modified or simply blocked.
An interesting idea. I'm not sure how it will work, but this is something employers always point to as lacking. From Paul Fain ... Grading Personal Responsibility
Grades earned by many students at Asheville-Buncombe Technical Community College will soon factor in “soft skills,” such as whether they show up for class on time or work well in groups. And next year the college will issue workplace readiness certificates alongside conventional credentials to recognize those skills.
Located in Asheville, N.C., A-B Tech, as it is commonly known, has developed a template that helps faculty members determine how to incorporate eight primary workplace expectations into grading, including personal responsibility, interdependence and emotional intelligence. Soft skills should count for 8 to 10 percent of grades in courses that adopt those guidelines, college officials said.


Sony still makes cassette recorders? Who knew! Sean Buckley ... Putting the cassette to bed: Sony to discontinue handheld tape recorders in 2013
The Walkman's retirement wasn't quite the death of the cassette tape, but the format's final days aren't far off: Sony's calling it quits on the tape recorder. Final shipments for the company's TCM-400, TCM-410 and TCM-450 cassette recorders are due early next year, marking the end of the product line.
- Posted using BlogPress from my iPad
Neat little application …. Scapy: a powerful interactive packet manipulation program:
Scapy is a Python program that enables the user to send, sniff and dissect and forge network packets. This capability allows construction of tools that can probe, scan or attack networks.
In other words, Scapy is a powerful interactive packet manipulation program. It is able to forge or decode packets of a wide number of protocols, send them on the wire, capture them, match requests and replies, and much more. Scapy can easily handle most classical tasks like scanning, tracerouting, probing, unit tests, attacks or network discovery. It can replace hping, arpspoof, arp-sk, arping, p0f and even some parts of Nmap, tcpdump, and tshark).
Scapy also performs very well on a lot of other specific tasks that most other tools can’t handle, like sending invalid frames, injecting your own 802.11 frames, combining techniques (VLAN hopping+ARP cache poisoning, VOIP decoding on WEP encrypted channel, ...), etc.
Two mythical beasts discuss Microsoft's new tablet ...
MACALOPE: Uh … OK. So … how’s it going with the Surface RT?
WINOTAUR: Great! Couldn’t be better. We’re well within the standard deviation on our sales projections.
- Posted using BlogPress from my iPad

Nice primer on whitespace spectrum from Ben Ward ... Whitespace Spectrum
Whitespace spectrum is a new way of offering large amounts of spectrum where the owner currently doesn’t or can’t use it. Opportunistic spectrum sharing allows swathes of TV and other spectrum currently lying unused to be accessed by users on a geographical and temporary basis (eg. in a specific location for a couple of minutes or months) by using coordination databases rather than auctions and long-term ownership. This spectrum has characteristics ideal for the Internet of Things and wireless sensor networks - long range, low power, good penetration, good bandwidth.
- Posted using BlogPress from my iPad
Interesting development from Bill Ray … Wi-Fi routers able to manage bandwidth by app are offered:
The latest wi-fi routers know which applications are asking for wireless connectivity and can prioritise those that matter while still letting data trickle to those which don't.
The technique, which maker Aruba calls "AppRF", looks at the packets to work out what each wi-fi client is doing, allowing the enterprise to decide which applications get priority access - so the busy BOFH can throttle the executives' video conferencing while ensuring his Call Of Duty pings remain low. Encrypted comms, such as MS Lync, are fingerprinted and so can be equally controlled even if the content of each packet is obscured.
From Leslie Horn … Cadbury Chocolate Will Literally Melt In Your Mouth, Not in Your Hand:
The bright minds in Cadbury's R&D department have done something amazing—they've created chocolate that won't melt.
… can be very powerful! Anonymous says FML:
Today, my husband quit his job as a university professor and picked up the graveyard shift at a rat farm so he could have more time during the day to play World of Warcraft. FML
From Kathlene Collins … a little long, but if you're in academia and are or may one day be a chair, so good info. Supporting Department Chairs:
People don’t become academics because they aspire to be department chairs, but every department needs one – and perhaps never more than in these economically challenging times. Many chairs complain that they receive no training and no support – even as senior administrators frequently fault chairs for not doing enough.
On Wednesday, November 28 at 1 p.m. Eastern Inside Higher Ed presented Supporting Department Chairs, a one-hour webinar focused not on blaming chairs, but on supporting them. Experts from The IDEA Center, which provided a range of training and evaluation programs for chairs.
Click here to download the slide deck for this presentation.
Great graphic from Dustin … How Frequent is Your Birthday?:
Very nice heat chart. I wonder what would happen if you filtered by geography? An awful lot of people I knew in northern NY were born 9 months after the cold dark winter.
More colorful Tableau version:
Yes, even your printer can be exploited!
From Lucian Constantin … Samsung printers contain hardcoded backdoor account, US-CERT warns:
Printers manufactured by Samsung have a backdoor administrator account hard coded in their firmware that could enable attackers to change their configuration, read their network information or stored credentials and access sensitive information passed to them by users.
The hardcoded account does not require authentication and can be accessed over the Simple Network Management Protocol (SNMP) interface of the affected printers, the U.S. Computer Emergency Readiness Team (US-CERT) said in a security advisory.
Joanne Jacobs … After university, community college:
Unemployed college graduates are heading to community colleges for associate degrees in nursing, medical technology, information technology and other high-demand fields.
Autodesk has been pushing out a bunch of amazingly powerful free iPad apps. Formit (see screenshots below) is just the latest. Imagine an architecture student or architect exploring their creativity anywhere, anytime.
As the saying goes … not your father's CADD!
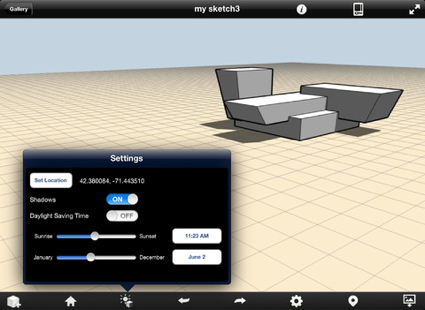

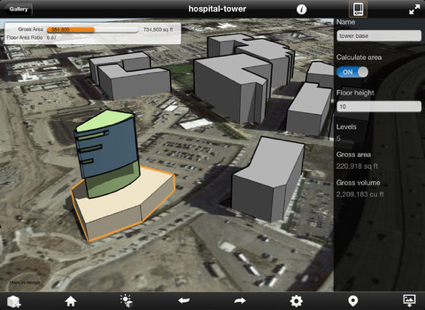
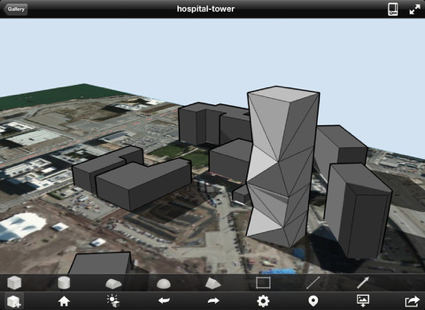
Autodesk FormIt for iPad on the iTunes App Store:
Autodesk® FormIt mobile app helps you capture building design concepts digitally anytime, anywhere ideas strike. Use real-world site information to help create forms in context and support early design decisions with real building data. Experience a continuous Building Information Modeling (BIM) workflow by synchronizing designs in the cloud for further refinement using Autodesk® Revit® software products and other applications.
Nice rundown by Michael Mulany ... Microsoft Surface vs. the iPad gen 4: The HTML5 Scorecard:
This week, we've been putting both the iPad gen 4 and the Microsoft Surface tablet through their paces to see how they stack up as HTML5 platforms. HTML5 is the next generation of web technologies that is increasingly being adopted to develop applications that can be written once and run on multiple operating systems, browsers and devices. Having comprehensive, high performance HTML5 support is now a "must-have" feature for new mobile devices. For end users, both these devices should deliver solid user experiences from well-designed HTML5 apps.
In our testing, we're happy to say that both tablets are solid HTML5 platforms. The Microsoft Surface comes with Internet Explorer 10 and Windows 8 while the iPad comes with Mobile Safari and iOS 6. Internet Explorer 10 on the Surface has a broad, well implemented HTML5 feature set that mostly meets and occasionally exceeds Mobile Safari's. On the performance front, the iPad 4 leads in JavaScript, interaction and Canvas performance: the Surface has a faster vector graphics (SVG) implementation.
Patrick Blampied has a Macintosh portable running OSX:
I took plenty of photos along the way which I’m going to turn into a post a week for the next few weeks. I’ll be covering the main hardware, mounting the screen, optical mouse conversion and the remapping/rewiring of the keyboard – which ended up being fairly involved.
Especially for the holidays!
From Leena Rao … Black Friday Online Sales Surged 21 Percent Thanks To Mobile Shopping, More Retailer Promotions And Personalized Deals:
After a particularly strong Thanksgiving for online sales, shoppers continued to look for e-commerce deals on Black Friday. IBM Digital Analytics Benchmark is reporting the final tally for Black Friday online sales: a surge of 20.7 percent growth in spending from last year. The biggest surge on Friday came from mobile consumers, with sales reaching 16.3 percent, led by the iPad.
Seems like Microsoft is doing everything they can to "discourage" users from installing alternative OSs on Windows 8 PCs.
From Jon Fingas … Linux Foundation vet explains setbacks in getting a Secure Boot key for Windows 8 PCs:
Linux fans wondering why they still don't have a friendly UEFI Secure Boot option for Windows 8 PCs won't get a solution in hand this week, but they'll at least get an explanation. The Linux Foundation's primary backer for the alternative OS efforts, Parallels' server CTO James Bottomley, has revealed that Microsoft's requirements for signed, Secure Boot-ready code are tough if developers aren't entirely onboard its train of thought. The Redmond crew demands a paper contract signature (remember those?), agreements on work beyond the relevant software and a packaging process that complicates attempts to use open-source tools. Bottomley has already overcome most of these challenges, although he's still waiting for a Linux Foundation-specific key that should theoretically clear a major hurdle. Whether or not that leads to a remedy in days or weeks is up to Microsoft; in the meantime, we'll take comfort in knowing that a signature is so far a convenience for booting into Linux, rather than a necessity.
Amazing! From David Pescovitz … 1951 digital computer restored and rebooted:
Wolverhampton Instrument for Teaching Computation (WITCH), a 61-year-old machine that was rebooted yesterday to become "the world's oldest original working digital computer." Originally operated at the Harwell Atomic Energy Research Establishment, it was moved in 1957 to Wolverhampton's Staffordshire Technical College where it was dubbed the WITCH. There it stayed until retirement in 1973 when it became a museum display before dismantling for storage. In 2008, the National Museum of Computing in Bletchley Park began to restore the valve-laden beast.
Good list! I think some of them are already out if not on their way out - can't remember the last time I used a landline phone or a fax machine. 15 Current Technologies A Child Born Today Will Never Use:
1. Wired Home Internet
2. Dedicated Cameras and Camcorders
3. Landline Phones
4. Slow-Booting Computers
5. Windowed Operating Systems
6. Hard Drives
7. Movie Theaters
8. The Mouse
9. 3D Glasses
10. Remote Controls
11. Desktops
12. Phone Numbers
13. Prime-time Television
14. Fax Machines
15. Optical Discs
From Jay Yarow … Apple TV Is 'Imminent' Says Jefferies (AAPL):
Apple's entry into the TV market is "imminent," says Jefferies analyst James Kisner.
Kisner talks about Apple TV in a note about Arris, a cable tech company.
"Our discussions with industry contacts suggest that at least one major N. American MSO is working to estimate how much additional capacity may be needed for a new Apple device on their broadband data network. We believe this potentially suggests an imminent launch of the Apple TV," says Kisner.
What's interesting about this wording is that it suggests Apple is going to be doing something over broadband, as opposed to normal cable.
By a whopping 700%! From Matt Brian … The end of slow public WiFi? Researchers develop new protocol that boosts WiFi performance by 700%:
Conferences, airports, cafes – they might offer free WiFi to visitors, but they are often sluggish in their operation because everyone else is hogging the connection.
This issue might become a thing of the past, after a team of engineers at NC State University (NCSU) announced the development of WiFox (via ExtremeTech), a new software protocol that could theoretically be added to existing Internet routers and is capable of boosting WiFi performance by 700 percent.
Traditionally, routers offer a single channel of data to users. When the access point receives an increased number of data requests, it becomes harder for it to send back the data it has requested. The access point could be programmed to give all pieces of data a high priority to clear its backlog, but then users have issues submitting new requests.
Data backs up, and the router has issues dishing out the necessary information to users. You may have experienced this when you turn up early to a conference, enjoy the public WiFi connection, and then get kicked off when the venue starts to fill up and you have to share it with everyone else.
NCSU engineers position WiFox as the software equivalent of a traffic policeman, ensuring that the data traffic moves smoothly in both directions. WiFox works by monitoring the traffic on a WiFi channel, intelligently detecting load issues and granting access to priority data when it detects a backlog of information passing backwards and forwards.
The team says that when they tested the software on a router in their labs capable of handling 45 users, it saw improvements of between 400 and 700 percent when it reached the maximum number of users.
700 up - 600 down … wow! Google Fiber is live in Kansas City, real-world speeds at 700 Mbps:
Mike Demarais posted this to Twitter during the first few minutes that Google Fiber went live in his Kansas City home.
From Kerry Doyle … Eight Emerging IT Certifications For 2013:
1. Big Data - (Certified Developer for Apache Hadoop)
2. Wireless Networking - (Certified Wireless Network Administrator)
3. Cloud - (VMware VCP-Cloud Certification)
4. Access Governance - (Novell Identity Manager Administration)
5. CyberSecurity - (Certified Information Security Manager, CISM)
6. Mobile App Development - (Secure Mobile Application Developer)
7. Green IT - (CompTIA Green IT Certification)
8. Data Analytics - (EMCDSA, EMC Data Science Associate)
From Ron … Old-school Okidata dot-matrix printer used for printing on Surface RT (video):
Microsoft has touted the Surface RT tablet to be excellent when it comes to USB connectivity and this video proves it. Ever thought you would see an old school Okidata dot-matrix printer (with parallel port connectivity!) again? In this video, we see this ancient printer connected to a Surface RT using a "Belkin USB to Parallel" cable and the printing works great! Check it out.
Interesting idea – just-in-time-printing … US army builds its own 3D printer:
By putting 3D printers behind the front line it hopes to be able to produce spares more cheaply and quickly than it can get them from manufacturers.
The army embarked on the project to produce its own printer as commercial devices were too expensive.
Early versions of the printer cost $695 (£436) compared to $3,000 (£1,880) for a commercial model.
The 3D printer has been developed by the Future Warfare centre at the US Army's Space and Missile Defense Command (SMDC) in Alabama.
From David Needle … 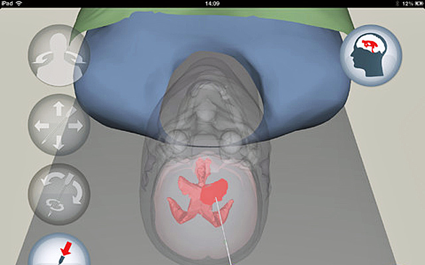
Free iPad App Helps Train Future Neurosurgeons:
The neurosurgeons of tomorrow can hone some of the necessary skills on the iPad, thanks to a new training app called VCath.
Developed by Bangor University in the U.K, the free iPad app helps neurosurgeons-in-training master an appreciation of the ventricular system in the brain.
The VCath app is designed to take a neurosurgical trainee through the steps of positioning and inserting a catheter into the brain of a virtual 3D patient. These steps are part of a procedure called “Ventricular Catheterisation,” which is used to drain fluid that has become obstructed within the ventricles of the brain.
Inserting a catheter at the correct orientation and depth so that it punctures the ventricles is critical to a successful outcome for the patient, notes VCath’s developer. It requires the neurosurgeon to have an excellent 3D awareness as the anatomy involved is not visible during the procedure.

Keep your electronics going through the next power outage with the Eton Boost Turbine ($60). This portable power pack features a 2000 mAH lithium-ion battery pack, a durable aluminum body, an LED charge indicator, a Micro-USB DC input for use with standard phone chargers, and your choice of one of four exterior colors. The big deal, however, is the built-in hand turbine power generator, which lets you juice up the battery, no electricity required.
Rocky Agrawal on Why I’m returning my iPad mini – surprise ending below
After less than a week, I’m ready to return my iPad mini.
I already have five tablets in my single-person household, including all three previous generations of iPads and a Google Nexus 7. I thought the mini would fill a small niche in my tablet needs, such as controlling my TiVo or Sonos system. So I bought the low-end 16GB Wi-Fi only iPad mini. I was wrong.
I like it so much that I’m going to return it and get a 32GB 4G iPad mini. I expect it will become my primary tablet. I’ve had various tablets since the Newton MessagePad 110. I’ve spent a lot of time with iPads, the Nexus 7, and Kindle Fire. iPad mini is easily the best tablet ever.
11/07/12 PHD comic: 'Punctuation mark decoder':
Piled Higher & Deeper by Jorge Cham For the latest news in PHD Comics, CLICK HERE!
(Via PHD Comics)