I've signed up for the free Stanford Cryptography course offered for free online through Coursera. This is one of a number of courses being offered through Coursera:
I teach networking and wireless courses where we introduce the concepts of encryption and cryptography, but not at this level and to this depth. I felt it would inform my lectures and enrich my own understanding to participate in ("take") this course. My Masters and PhD work both required a great deal of high-level math, but it's been nearly 20 years since I've done that sort of math on a day-to-day basis. Likewise my programming skills – I used to be quite the Fortran programmer – have no doubt atrophied. In addition to my interest in the content of this course, I'm very interested in the quality of the course and the quality of the online delivery. I hope to be able to learn some new things that I can bring to my online and web-enhanced courses.
Over the next 10 weeks, I'll be posting my experiences in this online course – I encourage you to register and follow along.
The course, taught by Dan Boneh, which begins tomorrow March 12th, consists of "Video Lectures" (along with the slides themselves), "Problem Sets" and a "Discussion Forum".
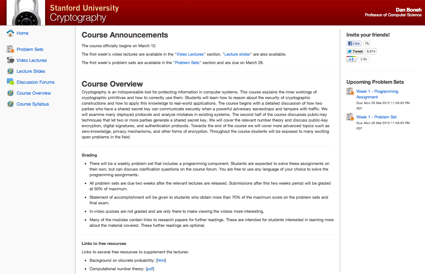
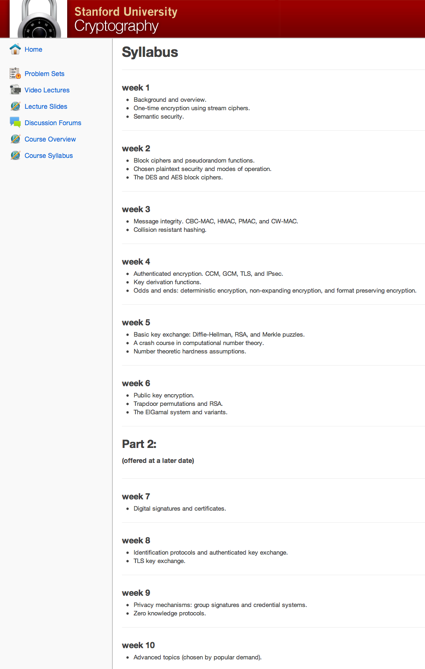
The course is split into two modules and scheduled to run for 10 weeks:
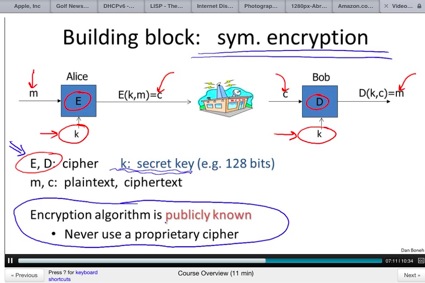
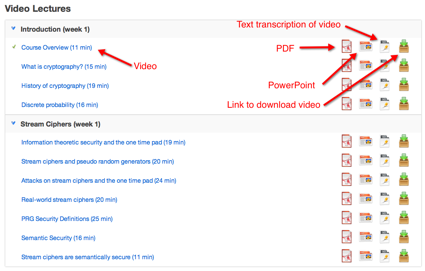
The Video Lectures, which are delivered in small bite-sized pieces, are available online and can be downloaded. The slides are available as PDF and PowerPoint, along with a text-based transcription of the video (great for ADA compliance!).
A great feature in the preferences in the ability to toggle the format of the videos – either Flash or HTML5.
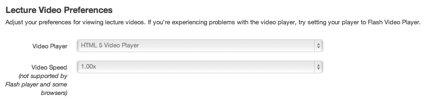
The HTML5 version looks great on an iPad – even without a Retina display: